Creating a Group Policy
Creating a Group Policy
- Navigate to Network-wide > Configure > Group policies.
- Click Add a group to create a new policy.
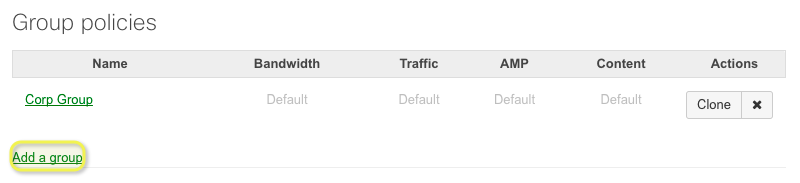
- Provide a Name for the group policy. Generally, this will describe its purpose or the users it will be applied to.
Ex. "Guests," "Throttled users," "Executives," etc. - Modify the available options as desired. Unless changed, all options will use the existing network settings.
- When done, click Save Changes.
The group policy listed will now be displayed on the Group policies page and made available for use. Remember that a group policy has no effect until it is applied.
Example Group Policies
The following examples outline two common use cases and how group policies can be used to provide a custom network experience.
The following example is meant to demonstrate how a group policy could be configured on a network to limit the access and speed of guest clients. This policy would accomplish the following:
- Limit client bandwidth to 2Mbps up/down
- Deny access to the internal network (which uses the 10.0.0.0/8 address space)
- Block all peer-to-peer sharing applications
- All other settings would be inherited from network defaults (such as security and content filtering settings)
Bandwidth limit cannot be set lower than 20 kbps.
It is not possible to enter multiple comma-separated ports in group policy custom layer 3 firewall rules. Ports must be in the range of 1-65535, or "any."
Executive Users on Wireless
This example demonstrates how a group policy could be used on a wireless network to provide executive users with more freedom and special treatment over other users. This policy would accomplish the following:
- Remove bandwidth restrictions
- Disable hostname visibility
- Remove layer 3/7 firewall rules
- Provide QoS tagging for voice and video-conferencing traffic.
- Remove the splash page requirement
- All other settings would be inherited from network defaults
Related Articles
Reboot a Device or Group
Create a Group for reboot of devices in Cisco Meraki
Secure QR Guest Wi-Fi Step 2
Navigate to SplashAccess : Secure QR Guest Wi-FI The QR code system needs to be deployed in three steps , we need to store all the information within Splash Access in relation to the Location of eacj network and the SSID tags together with the Group ...WebSite Terms
1. INFORMATION ABOUT US This Website is operated by Ormit Solutions T/A SplashAccess a company registered in England under number 07892585 and whose registered address is 2a Church Lane, Leyland, Preston PR253EJ, and whose registered VAT number is ...